This is why you do staged rollouts of updates… not the entire planet at once.
And don’t have automatic updates enabled for critical infrastructure.
So true, this really highlights the risk of updates impacting critical systems vs critical systems being exposed to critical vulnerabilities. Its a real balancing act.
It actually highlights the risk of having unaudited third party software running on your critical infrastructure
I don’t know exactly how crowd strike works, but this sounded like a “virus signatures” update (IE not a software update per se). And thats what caused the issue.
I think “real time virus protection” is why people use it so they expect the signatures to get updated asap/with little to no human intervention.
This is a crowd strike epic fail…for how they let their software blue screen systems with a virus signature update.
No, you run Linux with automatic secutity updates turned on
Can somebody explain why the down votes?
Mostly because it’s simply not that easy. Devs go where support is at and follow market share (2000s era Mac gamer memes.)
If you look at the Linux community as a whole it’s a wasteland of competing parties and standards. So it’s not developing for linux it’s developing for distros^hardware.
Windows is shit and it’s pretty well known that it’s getting worse… but it’s still the standard and unfortunately until Linux starts unifying and becoming more stable for developers it’s unlikely to become more compelling for the broader market to switch to.
TLDR; every time a new conflict breaks out hop in that thread and say “give peace a chance” and see how well that gets received.
Windows is actually steadily improving from a security point of view. MS is finally starting to deprecate ancient garbage like NTLM, UWP apps are sandboxed and there’s even talk of rewriting core libraries in Rust to make them memory safe.
This is true enough. In general though I think it’s finding a tipping point between investors and having a good OS. Per the usual every other OS pattern they follow it probably will be on the struggle bus until the next version.
Are we talking linux deskop for usage at end points?
Seems odd, we CAN run servers on it but end points can’t be done properly.
I don’t know shit about shit but linux desktop was a pleasant surprise as a gamer.
Steams been a massive contributor to that.
It’s a demonstration that if we focus on a common goal that Linux development can actually be pushed forwards. So this is definitely an improvement for end users - and I expect it will improve in the future… But broadly speaking there are too many requirements for some level of troubleshooting knowledge.
That comment you answered to is full of shit, desktop Linux works fine for many companies. And no dev ever chooses Windows lol
A wasteland of competing standards lol
More like a bountiful harvest. Even the dogshit programs windows users buy are mostly made with FOSS libraries.
The real answer is windows apologists don’t want to hear Linux users gloating about how this never happened to linux, and how dogshit their beloved os is
Because “just run Linux lol” is unrealistic and naive, it gets said on every thread, and it gets incredibly tiring.
i guess running Windows PC is realistic and smart lol
When I have a very large, very expensive piece of manufacturing equipment whose control software only runs on Windows, yes, it is.
specific use case requires specific set up…
Can someone in non marketing terms explain what the fuck CrowdStrike Falcon Sensor is? I literally never heard of this company or product before.
It’s basically corporate anti-virus software. Intended to detect and prevent malware.
Apparently it’s the next iteration of AI based antivirus where it uses smart algorithms to detect system behaviours and makes assessments on whether they’re malicious or not
Apparently it’s the next iteration of AI based antivirus
CrowdskyStrikenet
I know there is a lot of marketing fluff, but yes, it is an EDR. Which means instead of just checking file signatures against a database if known bad stuff, it actually examines what applications do and makes a sort of judgement on if it is acting maliciously or not. I use a similar product. Although the false positives can sometimes be baffling, it honestly can catch a legit program misbehaving.
On top of that, everything is logged. Every file, network connection, or registry key that every process on the computer touches is logged. That means when something happens, you can see the full and complete list of actions taken by the malicious system. Thus can actually be a drain on the computer, but modern systems handle it well enough.
What do you use? I’d be interested in that sort of thing
SentinelOne. They are more reseller/MSP friendly, but the product is very similar to CrowdStrike.
We also use S1 and while it does often flag false positives, that’s a whole heck of a lot better than the alternative. Also I have not noticed it being very resource intensive.
It’s overhead is more subtle than task manager can tell. Because of all its watching and monitoring, it slows down applications themselves. Task take longer. Sometime it is by a trivial amount, but I’ve been able to measure a notable difference in some task with and without S1, even if task manager says all is well.
obviously, A.I consider microsoft as a malicious software. Sometimes, A.I is very accurate 😁
Is it less expensive than ransomware though?
Yes
By a wide margin
Ransomware you have to pay $10,000 every few years. Crowdstrike you have to pay $1,000 per month. Same number of outages for both. /s
Add some extra zeroes to that ransomware figure…
Can you tell whether this update was delivered by Crowdstrike’s own update delivery pipeline of via Window’s update pipeline?
Absolutely nothing to do with windows pipelines or Microsoft
Okay, thanks. There was a parallel Microsoft outage, so I thought they were somehow linked.
Crowdstrike updates don’t come through Windows Update.
It checks for malicious falcons in your system’s level 4 aviary cache.
Ha ha! Well done!
It’s software put on every machine so that the company can quickly isolate it if/when something bad happens (or it falls out of security compliance). To do this is requires a constant Internet connection, insanely high privileges on the machine and frequent updates to be appraised of risks.
That risk update went off the rails and into the next state.
I work in QA on the night shift at a video game company. It was absolute chaos at work tonight lmao we only had a grand total of 6 working PCs between all of us
Company spyware. We have that on our devices. They used to have an “about” stored locally on the app, but removed it and a web connection is required to view the docs. Basically says it downloads/sees everything on your device and checks for threats. Thing is a few people have been fired for having things in their devices they shouldn’t. I didn’t ask what it was, nor did I hear how these things were “threats”, but nonetheless they were fired. Too many people treat company hardware like “free device, bro!” and put all sorts of personal stuff on the device. Most industries it’s probably not too big of a deal, but for mine if there’s an incident that happens when you were busy watching Netflix or something instead of doing your job you’re fucked. First thing they’ll do is check your device and crowdstrike to see what you were doing, and even if you weren’t watching Netflix all your personal data will be exposed.
They definitely could, but most cybersecurity departments are paid too much to worry about minor items like that. If HR tells us to look into a specific user and gets the proper approvals so that everything is in compliance, we’ll definitely get someone on the team to do it, but otherwise if we happen to see evidence of unapproved usage, we’re mostly going to overlook it unless it could lead to something dangerous to your machine or the company as a whole.
EDRs like Crowdstrike can see very very nearly everything you do though, definitely everything you would care about.
Yikes. I feel sorry for all the help desk and support staff that has to deal with this chaotic mess all day.
On a Friday !
What kind of criminally incompetent psychopath rolls out a global update on a fucking Friday afternoon?
Is the CEO of CrowdStrike Satan?
They push updates every day. Attackers don’t take Fridays off.
I have heard that Friday afternoon can be better because it gives you a full weekend to put out any fires before business hours start again.
That’s assuming it’s a small error that doesn’t roll on into the week anyway.
They’ll need that beer.
Yup, my phone is nonstop going off with slack messages and tickets. Time to mute it for now
What a striking name… CrowdStrike heh. They definitely live up to it!
More like CrashStrike
This is going to turn out it was a hack in several months right?
Won’t take that long, security researchers are already decompiling the update to see if it was malicious or incompetence.
This is going to be Solarwinds all over again I can just smell it.
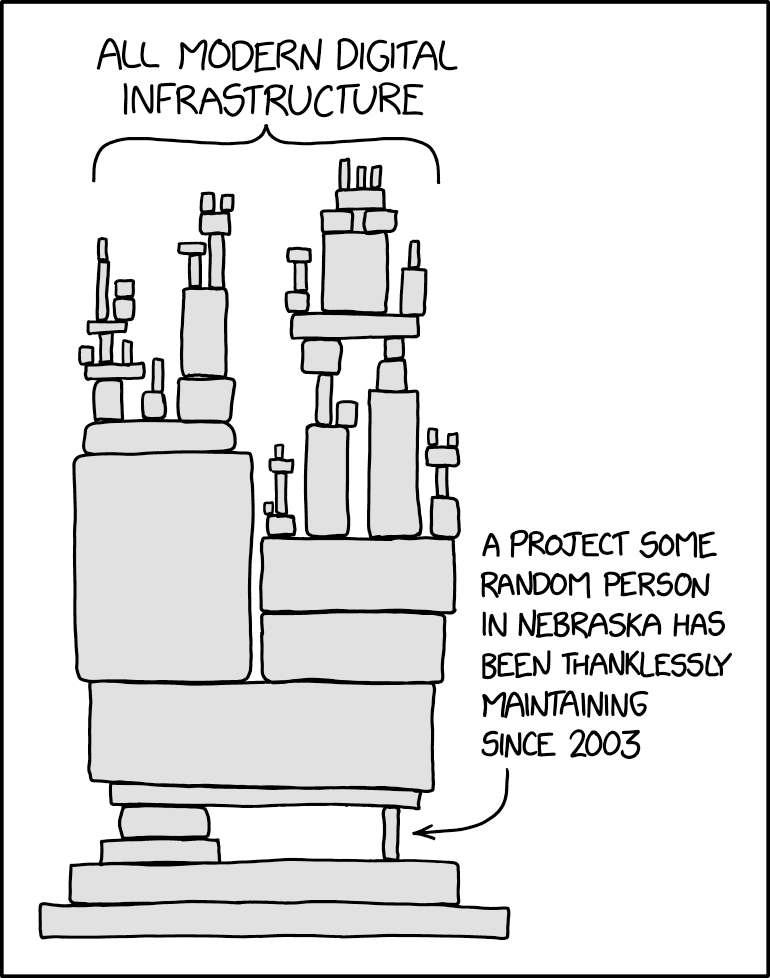
Source: xkcd - “Dependency” - https://xkcd.com/2347/
Yeah… applicable on soo many levels.
You won’t find the incompetence in the software no matter what.
If you fail to assume that the software contains issues – if you fail to understand that your software is made by humans and humans make mistakes, not because they’re bad but because they’re human – and if you fail to implement mechanisms to feel gracefully with inevitable failures, THAT is the incompetence.
Failures are systemic.
Oh yes I make those failures myself, testing and staging and limited release schedules save my human failures from breaking the world
Systemic failures are incompetence.
No idea why this relatively banal truth is getting so many downvotes
One funny thing about humans is that they aren’t just gloriously fallible: they also get quite upset when that’s pointed out. :)
Unfortunately, that’s also how you end up with blameful company cultures that actively make reliability worse, because then your humans make just the same amounts of mistakes, but they hide them – and you never get a chance to evolve your systems with the safeguards that would have prevented these.
Hacks of this grade tend to be targeted, this is most likely incompetence.
A lot of companies will get calls from the “provider” offering help with mitigation so that additional features can also be installed. This is a time to be extra wary.
Edited: spelling
deleted by creator
Think big. This may have had a target. But hitting the target only wasn’t possible so everyone got hit.
It’s possible those responsible only had this weapon that was capable of hitting the target, maybe the plan was to disrupt world flights to make someone late tomorrow, who knows. Maybe poo-tin or Xi-the-Pooh wanted to hit America and its allies?
A state actor will use more precise techniques to attack specific targets. Think SolarWinds and Stuxnet.
Ransomware doesn’t apply here and tends to depend on phishing first anyway.
Even terrorists have specific targets in mind.
So it’s either Bond villains or incompetence.
Edit: The only way i can fit your comment would be an incompetent script kiddy. Even then, doesn’t make sense as all systems were not directly attacked, as would be the case, but rather through what would have to be a side-channel attack, so no.
Never attribute to maliciousness that which can be explained by incompetence.
That said, I’m sure the Crowdstrike CEO is currently on a phone call with three of their pet Congresscritters asking if they can get a $100M grant to harden their systems against Russia/China/NKorea/Antifa interference right now.
“Senator, we were hacked by gay furries.”
“We need to get more of our own gay furries! There’s a gay furry gap!”
If I ever become a super 1337 hacker I’m going to setup all of my exploits to look like it could be regular mismanagement, thanks for the advice
While being simultaneously gang…handled by the unnamed 3-letter agencies representatives
I’ll just quietly leave this here: https://www.crowdstrike.com/blog/crowdstrike-google-cloud-expand-strategic-partnership/
Ca-caw!
Looking forward to the Kevin Fang video in a few years.
Crowd Strike’s Final Fantasy
Crowstrike Onstrike
That’s a shame.
So cool